You may ask yourself; why would anyone want to track that? Similar to the real world, knowing who holds the weapon makes it easier to prevent an attack.
We mostly use the intelligence (as in “Contextual-Threat Intelligence”) to make quicker decisions if to allow or block a specific source IP address or payload carried in the packet from a specific source IP.
I looked at data we collected between 1st of January 2020 until 29th of February 2020. A majority of the devices (scanners / loaders) are home-user devices.
Which cities has the most infected devices scanning for new targets to infect, a.k.a Scanners
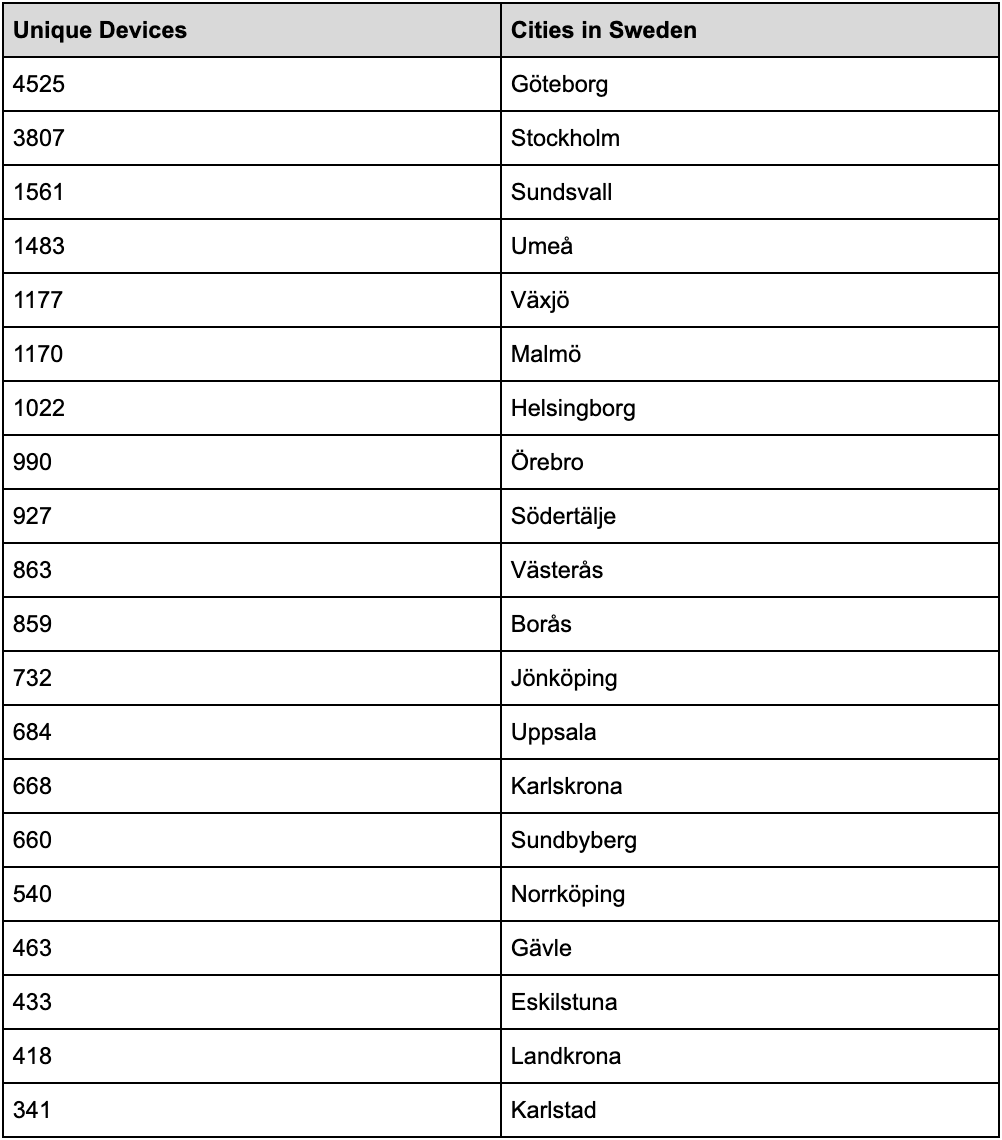
Which cities has the most infected devices publishing the weapons (malware), a.k.a Loaders

Which weapon (malware) is the most common spread via devices in Sweden
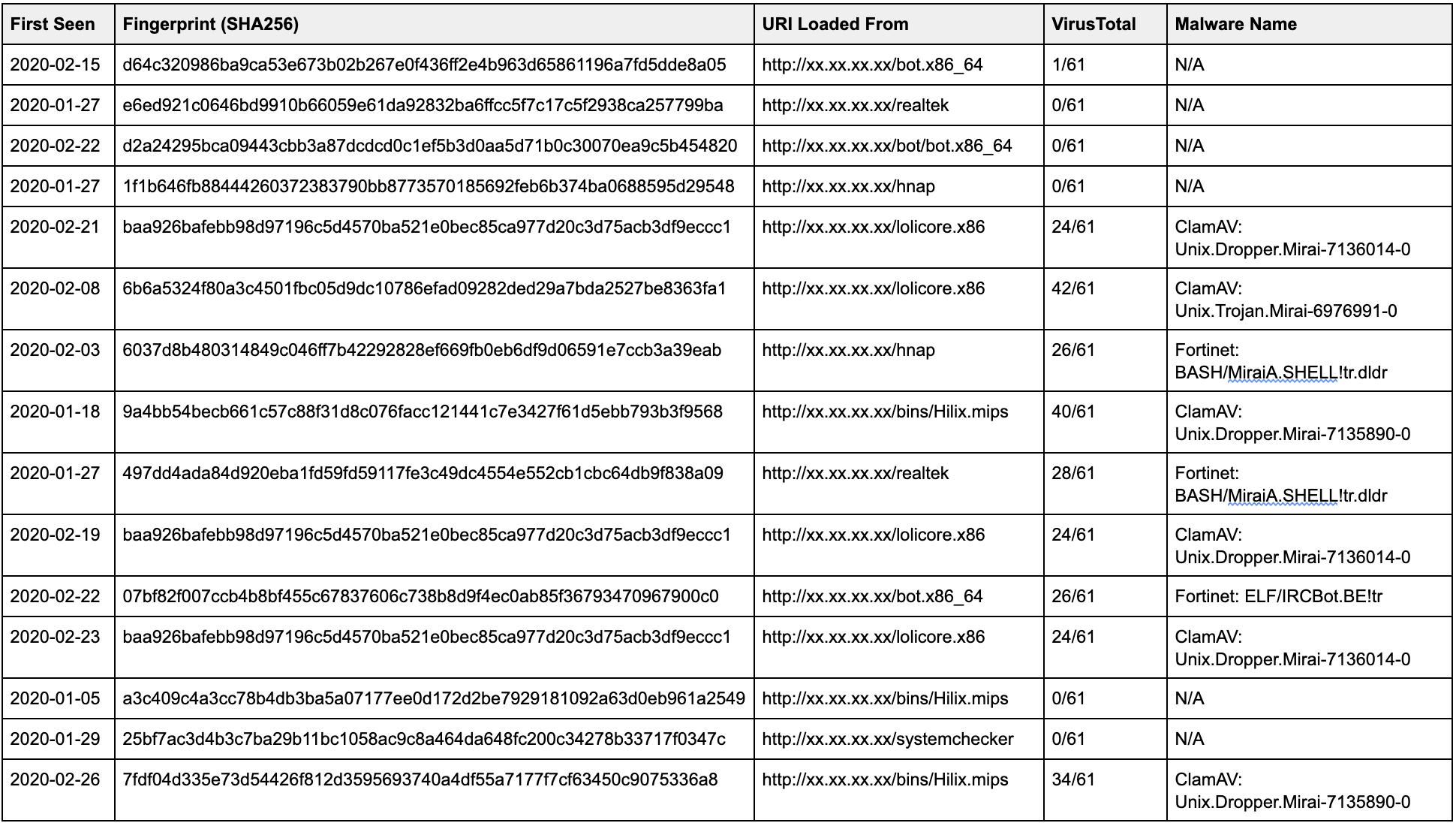
Maybe that last table requires some additional explanation.
First Seen: First time we at Baffin Bay Networks saw the malware being active or tried to infect a device protected by us or tried to infect a sensor in our global sensor network.
Fingerprint: This is a hash of the malware file in SHA256 format. It uniquely identifies the malware.
URI Loaded From: The URI that the malware is loaded from when a scanner manages to exploit a vulnerable device.
VirusTotal: This is the number of AV engines VirusTotal claims detected the malware.
Malware Name: If the malware was discovered by any of the VirusTotal engines we took “display” name for 1.) ClamAV, 2.) Fortinet. There are many more names available as most vendors have their own names of discovered malwares.
Let me know what you think and if you have need of our data or ideas of other articles we can publish.
One thing I was thinking of publishing is the correlation between the Covid-19 ("corona") outbreak and the activity / inactivity of the weapons we are tracking.
Join our event on Thursday by signing up here